Safe vs Weak Passwords: Could you be hacked in the next 5 minutes?

Why do people use weak passwords?
It’s no secret that most people prioritize convenience over security. When it comes to passwords, people like to use their cat’s name or their birthday — something easy to remember. They also don’t want to remember a bunch of different passwords, so they recycle that same password and use it everywhere. When weak passwords are the preference, security becomes an oversight.
How hackable is my password?
That depends. If you are using an email platform, any random combination of letters and numbers probably won’t get hacked as long as you don’t use the same password elsewhere and your password isn’t discovered in a data breach.
“The strongest passwords are at least 12 characters long, contain uppercase letters, lowercase letters, numbers and symbols, and do not incorporate personal details.”
If you’re using your name and birthday as your password, hacking bots can discover these kinds of details in minutes. One of the most common password guessing bots simply tries your name and a four-digit year. That’s less than 100 combinations since the year you were born, and covers most dates that are important to you.
So, how hackable is your password? Let’s talk about that.
Short passwords

A password’s length alone does not determine how easy it is to hack. It does play a role, though, especially in the context of brute force attacks.
If your password is compromised in a data breach, hackers can run a brute force attack locally on their machine. A weak password eight characters or less can be hacked in under a minute, which is why many experts recommend longer passwords. The longer the password, the more difficult it will be to brute force.
Simple passwords
Simple passwords consisting of all lowercase letters, numbers, or dictionary words can be cracked very easily.
If your password is more complex, it may be strong, but it will also be harder to remember. Most people typically prefer simple passwords or use a password manager to keep track of everything. This route has its own vulnerabilities, because if the password manager is breached, all of your stored passwords go with it.
Whether or not you use a complex password, one of the best ways to protect your account is with Two-Factor Authentication (2FA). This adds an extra layer of protection over your password. It’s more difficult to crack Two-Factor Authentication than even a long, complex password.
Recycled passwords
Don’t use the same passwords from account to account. If a hacker successfully gains access to one of your accounts, the first thing they will do is try the password against your other accounts. If that’s unsuccessful, they will attempt variants of that first successful password, or move on to social engineering techniques.
Back when FriendFinder Networks was hacked in 2016, over 412 million accounts (including 15 million deleted accounts) were exposed. Account usernames, emails, passwords, last logins, and IP addresses were all leaked.

If your username and password were found in the FriendFinder Networks hack, it could have implications far beyond immoral adult activity. If you used the same username for other services, hackers could scrape that information on the web to figure out what other services you use. Most importantly, however, would be if you recycled the same password. If you used ‘123456’ as your password for AdultFriendFinder, and reused that weak password for your email, online banking, and Facebook accounts, bots could crack your digital identity wide open instantly.
The bottom line: you don’t want someone to sit there and get into your email because you’re using the same password elsewhere. No matter how tempting it may be, never recycle passwords.
Sending passwords unencrypted
If you send your password unencrypted over the internet, there’s a good chance someone will sniff it. Virtually every coffee shop has a compromised router, and cybercriminals can even hack even your home router or IoT device to sniff passwords. When you set up your email account, you must use SSL (Secure Sockets Layer) or TLS (Transport Layer Security), and you never put a password web form unless it is HTTPS.
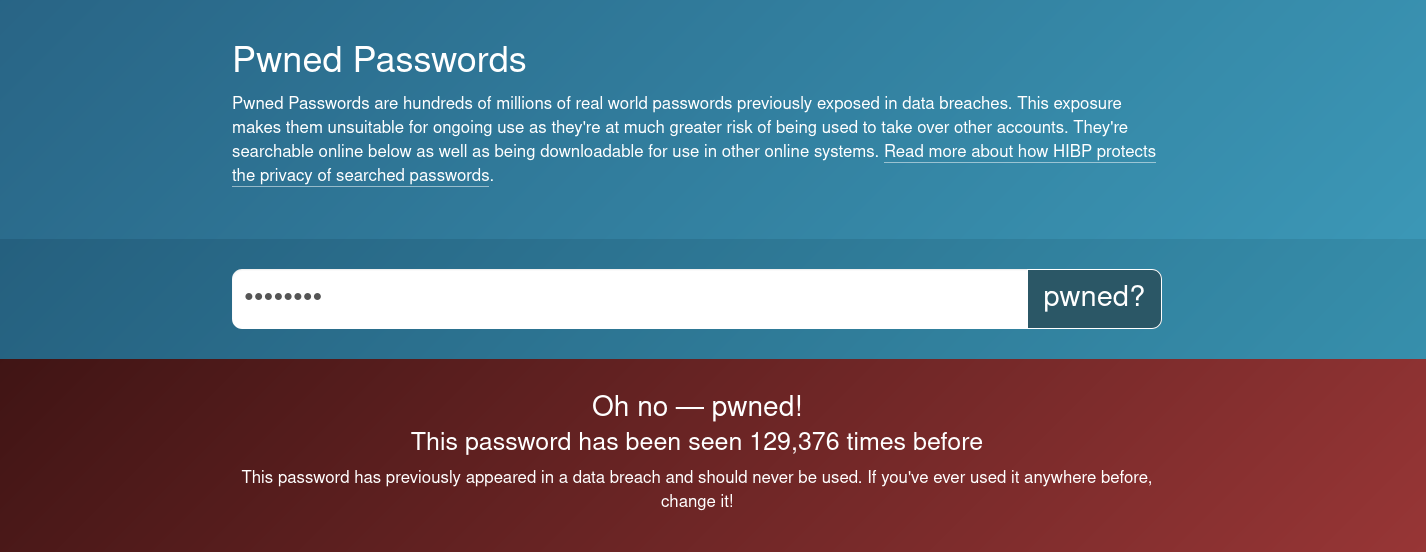
Has my password been leaked?
The best way to know is to check a site like haveibeenpwned.com that tells you whether your information has been compromised as part of a breach. There’s also a tab on the site for “Pwned Passwords” to check if your password has previously been discovered in a data breach.
“Never use your name or domain as part of an email password, and at least implement a combination of letters and numbers. Whenever possible, use Two-Factor Authentication — preferably Transparent Two-Factor Authentication (T2FA) methods like passing in a CLIENTID.”
If you need help with creating safe password complexity testers, you can always reach out to the team at LinuxMagic for examples, or validation code you can use.
What to do if your password has been leaked
Say you have an account on a website called “ilikecats.com” and a hacker infiltrates it. Your ilikecats.com account is now compromised.
Step one is to change the password for your email. If you created your ilikecats.com account with your email and reused its password, hackers could compromise your account quickly. This is why you never recycle passwords.
Step two is to change the passwords for all of your accounts where you used the leaked password. Then, change the passwords for all of the accounts you created using that email.
Step three is to enable Two-Factor Authentication (2FA) for all of your accounts, including the compromised one for ilikecats.com. This will add a layer of security over your password like a one-time password or biometric scan. Adding it over the compromised account may mitigate some damage, but those credentials are likely already available on the dark web.
How often should you change your password?

Email password compromise is a real problem, and you should get into the habit of changing your passwords regularly.
Generally, it’s a good idea to change your email password once a year. Many businesses advise changing passwords every three months, but if you aren’t compromised, once a year should be fine. For example, you could change your password when it’s time to change the batteries in your home smoke detectors!
Record your passwords privately in an encrypted note-taking program or physical notebook — and don’t forget to implement Two-Factor Authentication.

1 thought on “Safe vs Weak Passwords: Could you be hacked in the next 5 minutes?”
Comments are closed.