ASN Lookup: Finding the source of all that spam

Ever wonder where all of that incoming spam comes from? It’s easy to jump to conclusions about the source of the traffic, but what may seem like random domain names and servers might not be as random as you think. Fortunately, we as email administrators can always tell what IP the source came from. That IP belongs to a network, and that network can be attributed to an Autonomous System Number (ASN). By performing an ASN lookup, we can figure out who operates the network of that IP.
What is an Autonomous System Number (ASN)?
The internet is home to over 4 billion possible IP addresses, right? Not all of them are observable (many are either reserved addresses or operated by single large entities that aren’t really visible), but many of them are. A single IP can be responsible for hundreds of thousands of domains and email addresses, and every IP belongs to a network. As such, every network has information we can use. By researching which networks spam is coming from, you can not only discover interesting countermeasures, but take action against entire networks rather than IP by IP (if a network is abusing your server).
Typically, when you wish to know more about an IP, the “Whois” lookup tool can provide you some information. That said, not all Whois data is completely accurate.
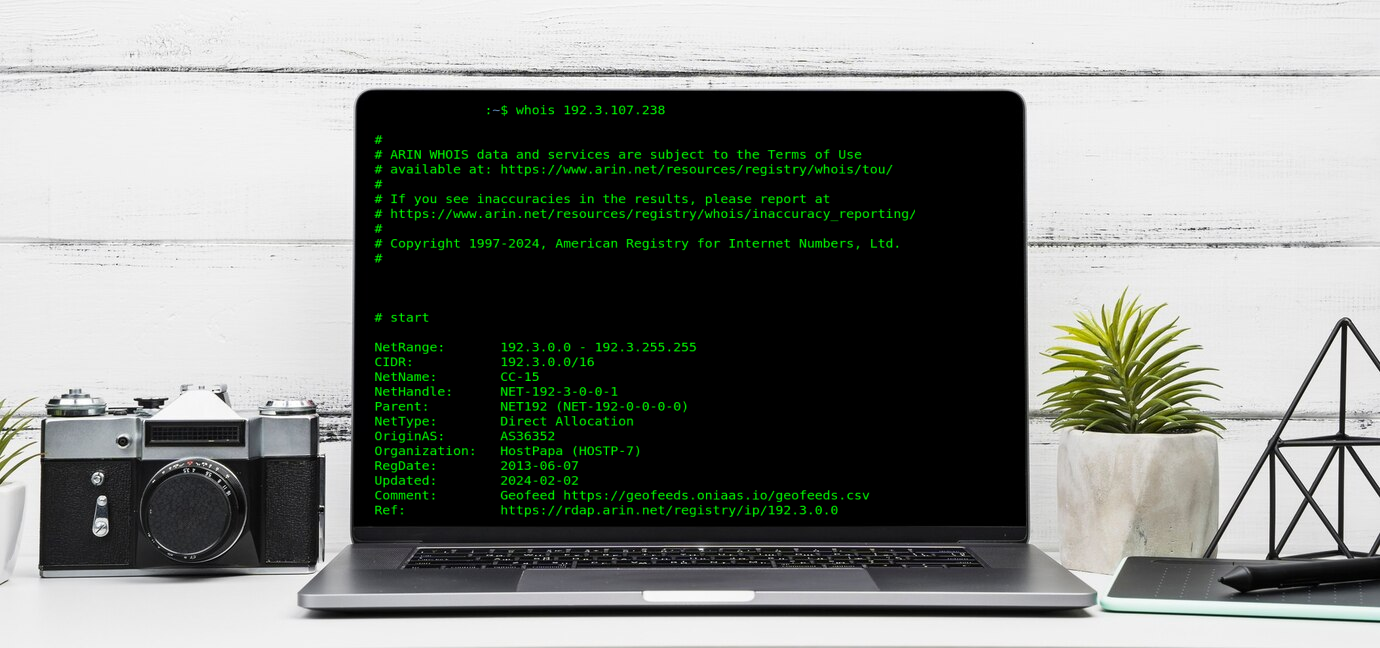
The Regional Internet Registries (RIRs) long ago agreed that every operator of networks must have a unique number for routing and interoperability reasons. Every IP on the internet has to have both a “route” as well as be associated with an “operator.” The ASN number reflects the latter.
In essence, Autonomous System Numbers (ASNs) identify those who operate networks on the internet. These are formatted as AS + number; for example, Microsoft’s ASN is AS8075.
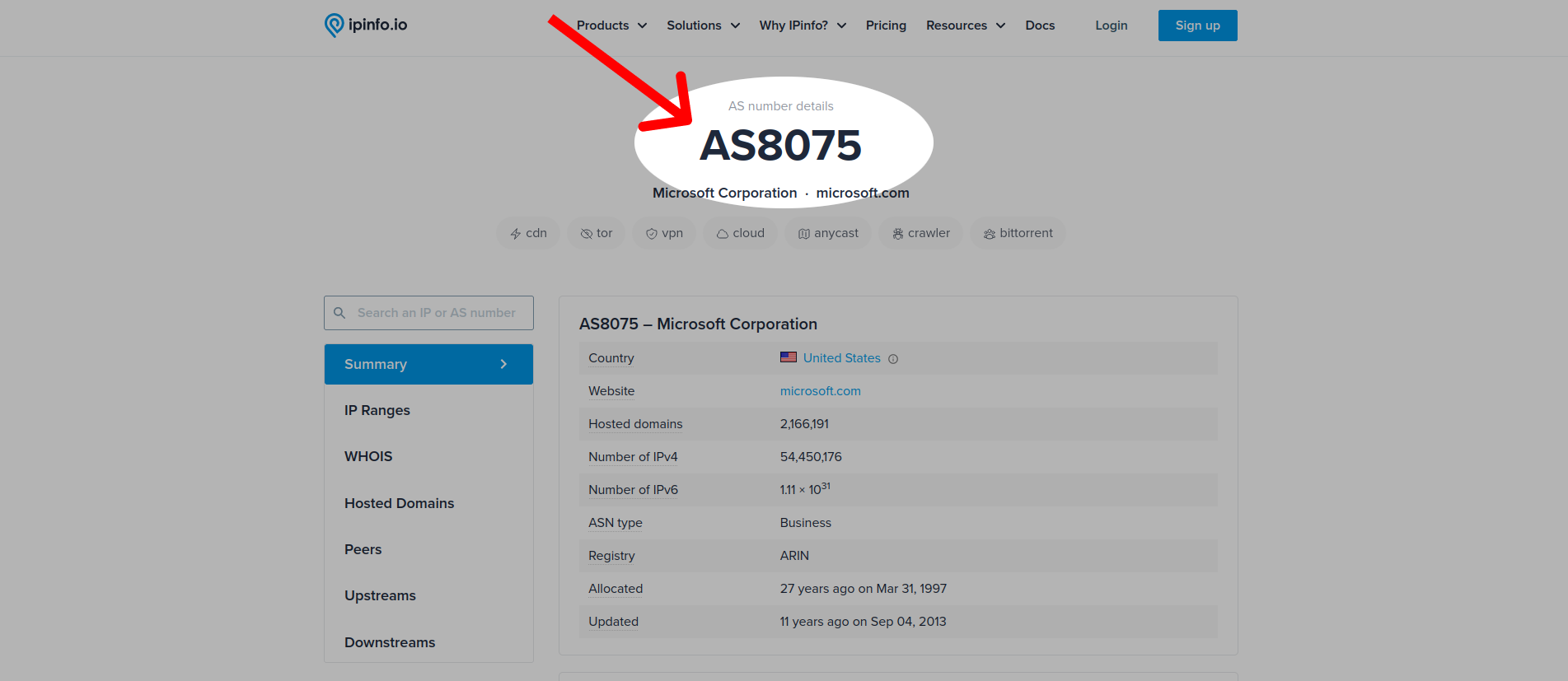
Without an ASN, the autonomous way networks talk to each other would not work. This information is also important to many internet protocols, including Border Gateway Protocol (BGP).
Because ASNs indicate who operates which group of IPs, they can be used in researching the abusive network.
RBLs: A long-term solution for spam and network abuse
Let’s say you get a ton of unwanted traffic from an IP. You could try blacklisting every domain or email address individually, but it’d be a lot easier to block the IP entirely. While there are only 4 billion IPs, there are almost unlimited domain names and email addresses.
Manually adding IPs to your blacklists can also be a huge time and energy sink. Every time you receive spam, you would have to manually go in, find the IP address, and block it. Real-Time Blackhole Lists (RBLs), like SpamRATS RBL, save you the work of having to identify and manually blacklist IPs.
RBLs are IP-based, but if enough IPs from a single operator are listed, you may want to know all of the IPs that operator is using. This is where an ASN lookup comes in handy!
If you use MagicSpam to protect your server, this comes with SpamRATS built in. It automates the process with utmost accuracy, as well as range, so you need not manually block IPs or emails. You simply install and forget.
What does an ASN lookup tell us?
To perform an ASN lookup, you must know the IP address responsible for sending an email. You can find this in your email logs, or by looking at the raw information in your emails. You can find the sender’s IP address in the email “header;” this is visible by going to the email and clicking View Source, View original, or the like.
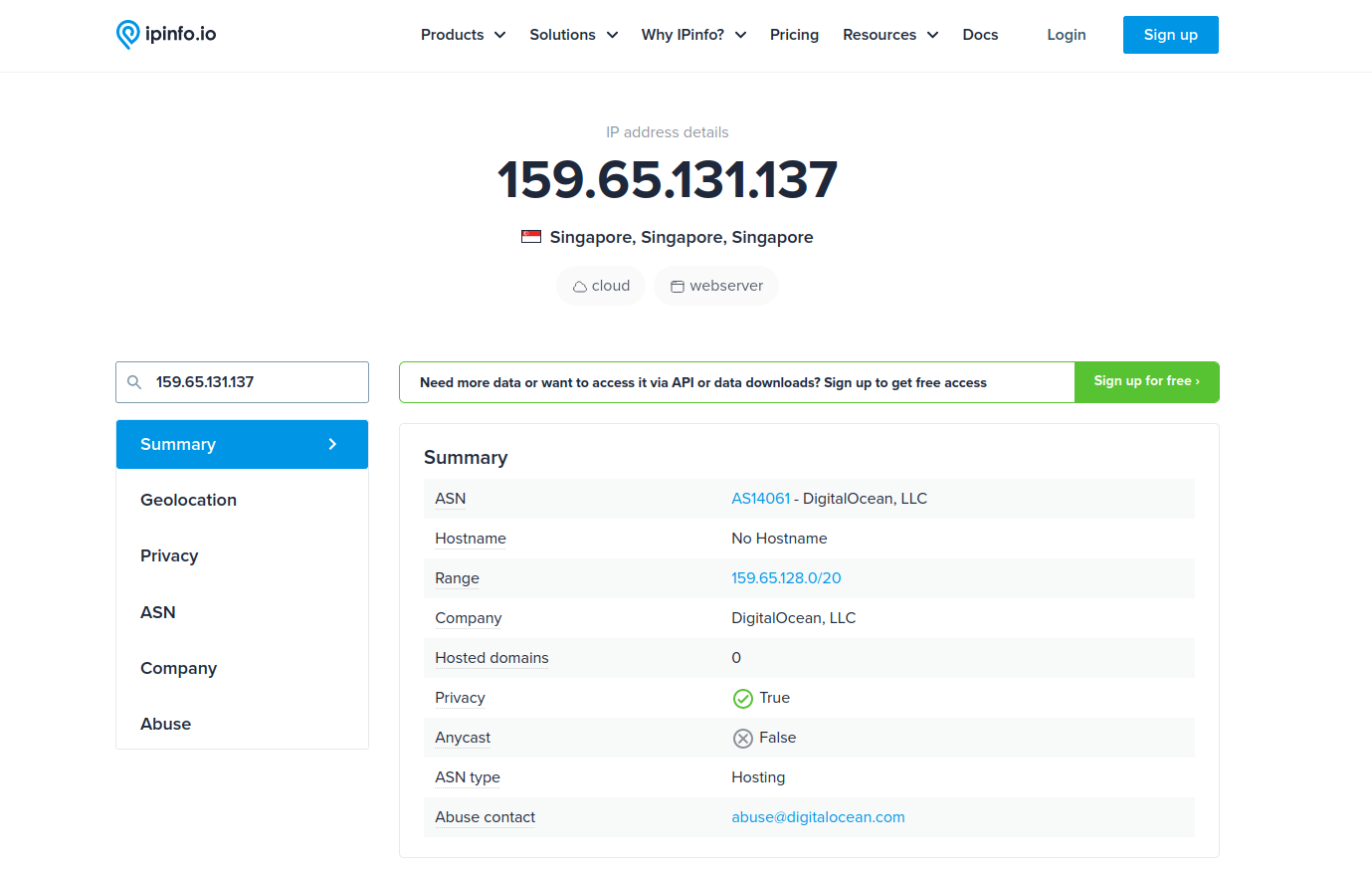
For example, here is a piece of common spam that you might see. The IP address is available in the header. In this case, it is 159.65.131.137.
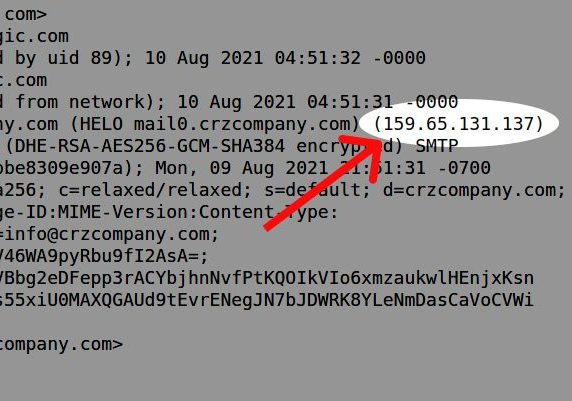
Once you have the IP, you can plug it into a reverse Whois, an online Whois lookup tool, or another 3rd party service to find out more. The American Registry for Internet Numbers (ARIN) administered this particular IP address as part of a network block back in 2017. When they transferred this block, they associated it with the operator’s ASN: AS14061.
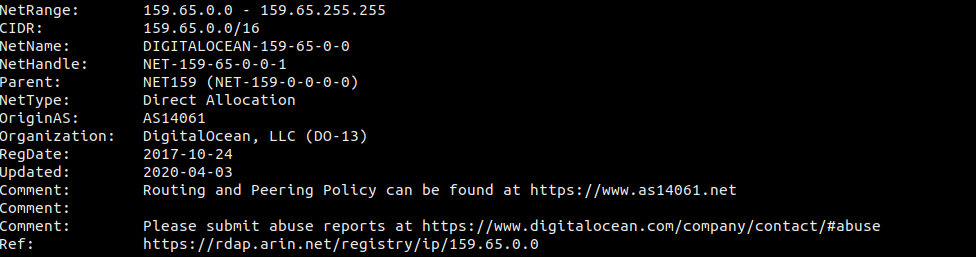
Services like custom Whois servers and ipinfo.io can offer details about the IP, network, operator, and even the region. In our example, though this block is under ARIN’s responsibility, it appears it’s being used in Singapore. We can also see the ASN associated with this operator, DigitalOcean.
Now, despite the RIRs’ best efforts, not all network ownership information you see in an ASN lookup is always accurate. Some companies have network blocks with vague, misleading, or even fake information. Reach out to the team at LinuxMagic if you need help identifying accurate, up-to-date ASN ownership information.
What to do after identifying the ASN
After identifying the ASN, we can find all the other networks operated by the same organization. To do this, you can use a custom Whois lookup from dedicated Whois services that provide this information.
whois -h whois.radb.net -- '-i origin' AS14061 | grep "^route\:" | cut -d\: -f2 | awk '{$1=$1};1' | sort -n | uniq
Running the above command, we can see that AS14061 (DigitalOcean, LLC) has 920 networks recorded as belonging to the same organization.
Why do we care about the organization with the ASN?
You would think that before an organization can get IP space, they must show they will use it for legitimate purposes and legal activities, right? Well, actually, no.
The RIRs (like ARIN, APNIC, and RIPE) choose not to get involved in this. It’s just not part of their mandate. On top of this, many large organizations with IP space “rent” parts of their networks to other companies. If they so please, these organizations can disregard what the IPs are used for, so long as the renting party has a proven need and the registration information is accurate.

As you may suspect, some of these organizations may “rent” IPs to nefarious actors. Of course, this would facilitate spam and malicious attacks. Remember, the laws are different around the world, so you can’t rely on the legal frameworks to prevent bad things from happening.
If an organization has a track record of hosting bad actors, should we trust any IP within its networks? Probably not, especially when the organization ignores or takes a long time to take down these actors. This is particularly frustrating for Information Security (InfoSec) researchers, as well as law enforcement. A simple search on Twitter/X will find lots of reports about various network operators.

We’ve recently seen more international efforts to go after some of these networks, especially ones used in obvious cybercriminal activity. In our industry, we call these kinds of organizations bulletproof hosts. These are hosting companies that either promise they won’t shut you down for your activities publicly, or have a history of doing nothing to address abuse reports.
Case Study: Hotmilk Studios LTD
An organization mentioned in recent InfoSec reports has reportedly been hosting malware. The IP 94.156.8.244 has supposedly been up for over a month without the complaints being addressed. A quick check on HetrixTools shows that IP appears on many RBLs. This also enables you to check other IPs belonging to the same organization by using the ASN lookup.
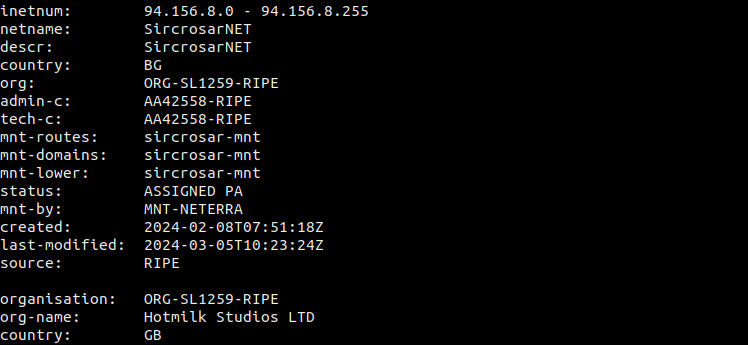
The Referral Whois (RWhois) provides additional details, like who is routing traffic to this ASN. In this case, that would be the company called NETERRA, the organization that supposedly owns this IP block (SircosarNET, Bulgaria), and the company currently listed as using it (Hotmilk, Great Britain).
Interestingly, when doing a lookup at RIPE, the responsible Regional Internet Registry, we see the following posted:
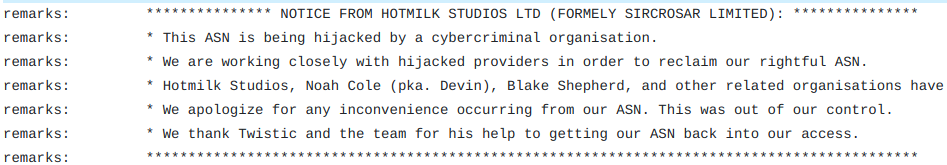
Given the situation, this should help you decide whether you want to play whack-a-mole as each IP comes across your desk, or apply the same rules for the whole ASN.
Recognize a bad ASN when you see one
ASN lookup is not guaranteed to be foolproof. However, the internet community reports many ASNs out there as threats. Many network operators go as far as to block all traffic from ASN operators that are deemed dirty, suspicious, or have a history of criminal activity. These include ASN operators that seemingly do not care about or address abuse issues.
You can check these out further in the SpamRATS RATS-NULL or SpamHaus DROP lists. You can even add them to your firewalls, or network layers. The easiest and most effective solution is to sign-up for a data feed that monitors ASNs, or use a product like MagicSpam to mitigate spam at the SMPT level.
But remember, one ASN could house hundreds of networks and thousands of IPs. Using ASN lookup tools is much easier than trying to address threats across all 4 billion IPs. Furthermore, if you know or find fake information used in registering an ASN, contact the responsible RIR with your evidence. Those IPs can be returned to the IP pool for the use by legitimate operators.
