cPanel Spam : How to Protect Your Server

Weeding out spam and malicious emails from a server is one of the most common hosting challenges. With the global average daily spam volume reaching a record high of 336.41 billion in 2021, it is clear what hosting providers and server administrators are up against.
As cPanel is one of the most widely used web hosting management platforms in the World, this article will focus on cPanel Spam Filtering Best Practices to reduce the amount of spam entering your mailboxes.
Read on to learn how to protect your server.
What is cPanel Spam?
Spam is a reality of the Internet, constituting 54% of all email traffic. It is not only annoying but also carries increased risk from threats such as ransomware, phishing, and business email compromise (BEC).
When trying to combat spam effectively, it’s important to have a comprehensive email security strategy that covers different stages in the email delivery process. From the point of connection all the way to the email being delivered to your mailbox, it’s important to have multiple layers of security technology targeting different spam characteristics in order to maximize protection and reduce risk.
For hosting providers, fighting spam is key to providing an excellent user experience and they must do everything in their power to succeed in it. That is why most hosting providers and web hosting management tools have built-in tools to fight spam. In the case of cPanel, the platform integrates a robust set of features to help you protect your server.
Reject cPanel Spam through Real-time Blackhole Lists
Real-time Blackhole List (RBL), also known as Domain Name System-based Blackhole List (DNSBL), is widespread technology with a long track record of being effective against spam. These RBLs typically track networks with poor email reputation due to them having a known history of bad practice, turning a blind eye to spammers, or being in the midst of a spam outbreak. Emails are rejected for delivery or flagged as spam when the IP address of the sending email server is listed on the RBL.
In cPanel, RBLs are checked early on in the email delivery process, right at the SMTP stage. Once you’ve added and enabled RBL, any incoming emails from sending email servers that match on that RBL will be rejected. There are many providers of RBL services which can be used free of charge, especially if you are a small email server operator. What’s important when evaluating the effectiveness of a RBL is its accuracy (ability to detect spam) and false positive rate (frequency of mistakes in detecting legitimate emails as spam).
As the server administrator, you can manage the RBLs used by your cPanel installation through the Manage Custom RBLs interface on the WHM Panel.
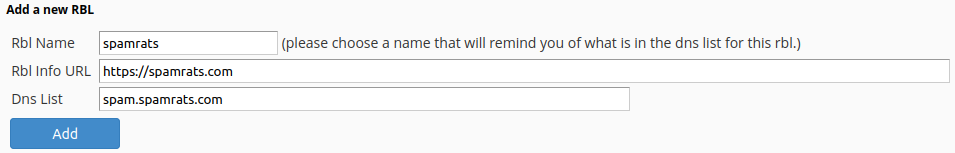
Once you find a RBL that you would like to use, add it to cPanel by entering the details of the RBL. We recommend the SpamRATS RBL for its high accuracy and low false positive rate.
You still need to enable the newly added RBL before it can start to protect your email server. This can be done through the Basic Editor in the Exim Configuration Manager interface.
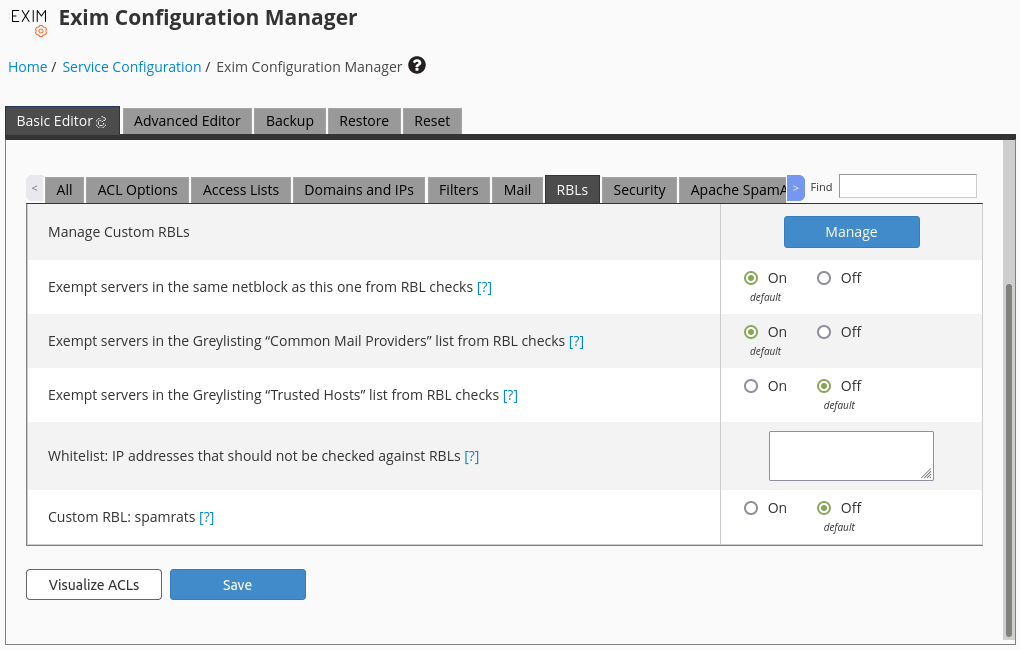
Simply select the RBLs section, search for the newly added RBL, and proceed to enable it.

It’s not recommended to use too many RBLs as each one of them requires a network lookup which increases the time taken to scan an email, especially when you’re dealing with thousands at a time. It adds up and may affect other performance metrics like overhead and bandwidth.
Filter away cPanel Spam using SpamAssassin
SpamAssassin is another tried-and-true email content filtering software technology. It is designed to estimate the likelihood of a message being spam using various tests to identify spam-like patterns. Based on these tests, it assigns a score to each message and prevents the ones that are most likely to be spam from being delivered to your inbox.
In cPanel, SpamAssassin checks occur after the email has been accepted for delivery but before the email is delivered to the mailbox. SpamAssassin is installed by default on cPanel server but stills needs to be enabled at the account level. Once enabled, any incoming email that scores higher than the configured thresholds will either be flagged as spam or rejected for delivery.
As a system administrator, you can enable SpamAssassin for all accounts with no option to disable it by toggling the Apache SpamAssassin™: Forced Global ON configuration through the Basic Editor in the Exim Configuration Manager interface.

Otherwise domain owners can activate SpamAssassin for themselves without the need to bother the system administrator through the Spam Filters interface.
Once SpamAssassin has been enabled on the account, any email that exceeds the Spam Threshold Score will be flagged as spam and have their subject line altered.
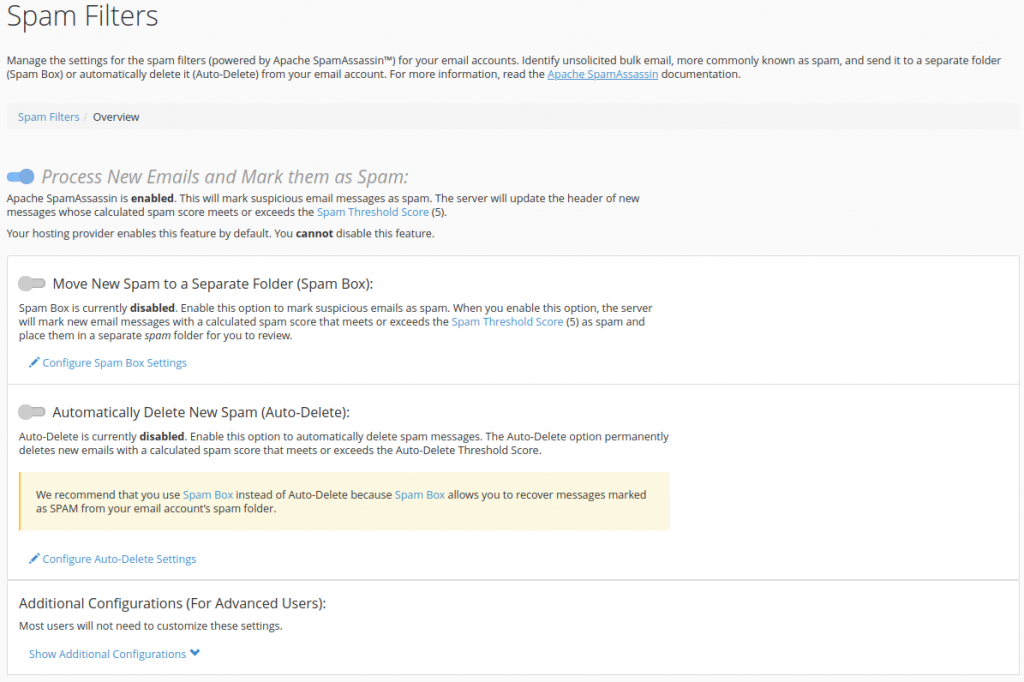
As a domain owner, you can additionally configure how emails flagged as spam by SpamAssassin are handled. The Move New Spam to a Separate Folder (Spam Box) feature will deliver emails flagged as spam to the spam folder, while the Automatically Delete New Spam (Auto-Delete) feature will delete emails which exceed the Auto-Delete Threshold Score.
Domain owners can also manage their whitelist and blacklist to specify the email addresses that should not and should be tagged as spam. Note that these whitelist and blacklist only applies to SpamAssassin, other technologies earlier on in the email delivery process may still reject the email.
By default the Spam and Auto-Delete Threshold Scores are set to 5. If you’re not familiar with adjusting the scores of rules, then it’s recommended to use the default threshold scores to maximize effectiveness as most rulesets are designed around the default threshold score.
Unless disk space is a major consideration on your server, it’s not recommend to use the Auto-Delete functionality as legitimate emails may accidentally be deleted. At least with using Spam Box, false positives are still delivered to the spam folder giving you an opportunity to review.
If you need to use Auto-Delete feature, then it’s recommended to use it alongside with the Spam Box feature but with different threshold scores. For example, set the Spam Threshold score to 5 and set the Auto-Delete Threshold Score to 7.
Stop malicious attachments in cPanel Spam with Clam AntiVirus
Clam AntiVirus (ClamAV) is yet another tried-and-true protection technology that focuses on email attachments. It has the ability to detect many types of malware including viruses and ransomware. Email with attachments that have malicious signatures will be rejected for delivery or have the attachment stripped from the email.
In cPanel, ClamAV checks occur after the email has been accepted for delivery but before the email is delivered to the mailbox. ClamAV is not installed by default on the cPanel server. Once installed, any incoming email with attachments that match a malicious signature will be rejected for delivery.
As a system administrator, you can install ClamAV through the Manage Plugins interface on the WHM Panel.
No further action is required once installed, ClamAV will immediately start scanning inbound emails for malicious attachments.
MagicSpam – A Comprehensive Email Security Solution
Despite the various built-in spam filtering tools available in cPanel, it’s not always enough and your server may still be getting a lot of spam. Oftentimes open-source technologies are unable to keep up with the rapid pace at which spam evolves.
When free email security solutions are no longer sufficient for your server, look to stop spam with a fully-featured email security solution. One that recognizes the importance of using multiple layers of protection against spam supported by an expert team of threat researchers who release daily email security updates.
MagicSpam is a fully-featured email security solution designed to run on cPanel servers – easy to install and even easier to use. MagicSpam integrates directly into cPanel without requiring any complex setup or customization to DNS, Firewalls, or MX records. MagicSpam offers multiple layers of protection with policy-based rules, reputation lists, rate limiters, and custom content filtering rules. In addition, MagicSpam even protects against compromised email accounts, the other half of email threats.
Conclusion
In this day and age, it’s clear that email is here to stay as the main communication medium for businesses of all sizes. Threat actors are aware of this and work hard everyday to exploit this fact and benefit off your misfortune. This highlights the need for organizations to take a good hard look at the tools available to them to thwart threats actors, built-in or otherwise.
