How to Prevent Spoofed Emails on cPanel Email Servers (Part 2)

This is the second part of a two-part article focused on Spam Filtering Best Practices to reduce the amount of Spoofed Emails entering mailboxes hosted on cPanel — one of the most widely used web hosting control panels in the World.
The first part covers the characteristics of Spoofed Emails and the ways threat actors use them to deceive victims — mainly how Spoofed Emails use forged sender information of trusted entities within the MAIL FROM and From Header to deceive and harm victims. By posing as a trusted authority figure, this email threat circumvents your natural skepticism leaving you more vulnerable against deception. Threat actors combine other threat techniques alongside email spoofing to deceive you into doing something that you would otherwise not have done leaving your business susceptible to financial and reputation damage. If you haven’t gone through the first part yet, you can find it here.
Now in the second part, let’s see how we can prevent Spoofed Emails in cPanel.
Use Sender Policy Framework (SPF) Verification in cPanel SpamAssassin
Sender Policy Framework (SPF) is an email authentication methodology designed to detect forged sender addresses during the delivery of email, specifically forgery of the sender address in the MAIL FROM. SPF Verification allows the receiving email server to check that an email claiming to be sent from a specific domain originated from an IP address authorized by that domain’s administrators.
cPanel comes with SpamAssassin as a built-in email content filtering tool designed to calculate a score for a message which estimates the likelihood of said message being spam using a variety of tests — including SPF Verification. As long as SpamAssassin has been enabled at the account level or global level, it’s very likely that you are already being protected by their SPF Verification Rules.
However, these SPF Verification Rules are not always effective at keeping out spoofed emails due to the their default scores. There is no guarantee spoofed emails that fail SPF Verification will be flagged as spam, as the default scores for these SPF Verification Rules does not exceed the default Spam Threshold Score of 5. Other scoring rules are needed in combination with the SPF Verification Rules in order to score high enough.
score SPF_NONE 0
score SPF_PASS -0.001
score SPF_NEUTRAL 0
score SPF_SOFTFAIL 1.5
score SPF_FAIL 4.0Also, whether a failed SPF Verification gets scored as SPF_NEUTRAL, SPF_SOFTFAIL, or SPF_FAIL is determined solely by the type of SPF ALL mechanism specified by the domain administrator.
| SPF Verification Rule | Trigger Condition | SPF ALL Mechanism |
| SPF_NONE | No SPF Record | N/A |
| SPF_PASS | Passed / Failed SPF Verification | +all |
| SPF_NEUTRAL | Failed SPF Verification | ?all |
| SPF_SOFTFAIL | Failed SPF Verification | ~all |
| SPF_FAIL | Failed SPF Verification | -all |
If the domain administrator specifies the Neutral SPF ALL mechanism, then the SPF_NEUTRAL Verification Rule triggers which means that no score is added even though SPF Verification failed. From our experience, it’s not uncommon for domain administrators to specify the Neutral or Softfail SPF ALL mechanisms in order to avoid email deliverability issues.
As such, we recommend taking back control by implementing this SPF Verification Email Security Policy.
All Incoming Emails that Fail SPF Verification are Flagged as Spam.
Regardless of the SPF ALL mechanism specified by the domain administrator, spoofed emails that fail SPF verification should never be delivered to the mailbox. This SPF Verification Email Security Policy can be achieved by overwriting the default scores of SPF Verification Rules at the global level or account level as a WHM Administrator and cPanel User respectively.
Though one implementation specific caveat would be with the SPF_PASS Verification Rule which plays double duty for both passed SPF Verification and failed SPF Verification with Pass SPF ALL mechanism. Fortunately the Pass SPF ALL mechanism is a well-known bad practice, so no legitimate senders use it in actuality. Also, don’t add a custom score for the SPF_NONE Verification Rule as not having a SPF record is not a indicator of threat and may cause false positives. It goes without saying that SPF Verification only works when domain administrators set SPF records for their email domains.
Overwrite SPF Verification Rule Scores at Global-Level (WHM Administrator)
As a WHM Administrator with Root access, you can implement this SPF Verification Email Security Policy at the global-level on the behalf of all your cPanel users. This can be achieved by overwriting the scores of the SPF Verification Rules by editing the SpamAssassin Global Configuration File at:
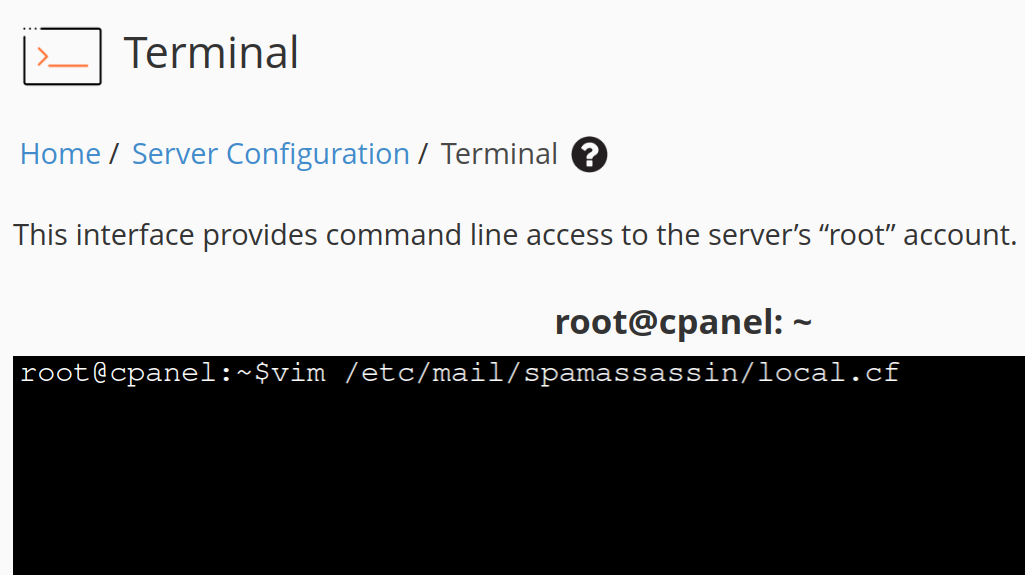
/etc/mail/spamassassin/local.cfSimply open the configuration file via the WHM Terminal and add new scores for the SPF_FAIL, SPF_SOFTFAIL, and SPF_NEUTRAL Verification Rules to the bottom of the file with a high score like 6 which exceeds the default and recommended spam threshold score by one to ensure all incoming emails that fail SPF verification are flagged as spam. If you don’t have the Vim text editor installed, use any other text editor that you’re comfortable with to edit the file.
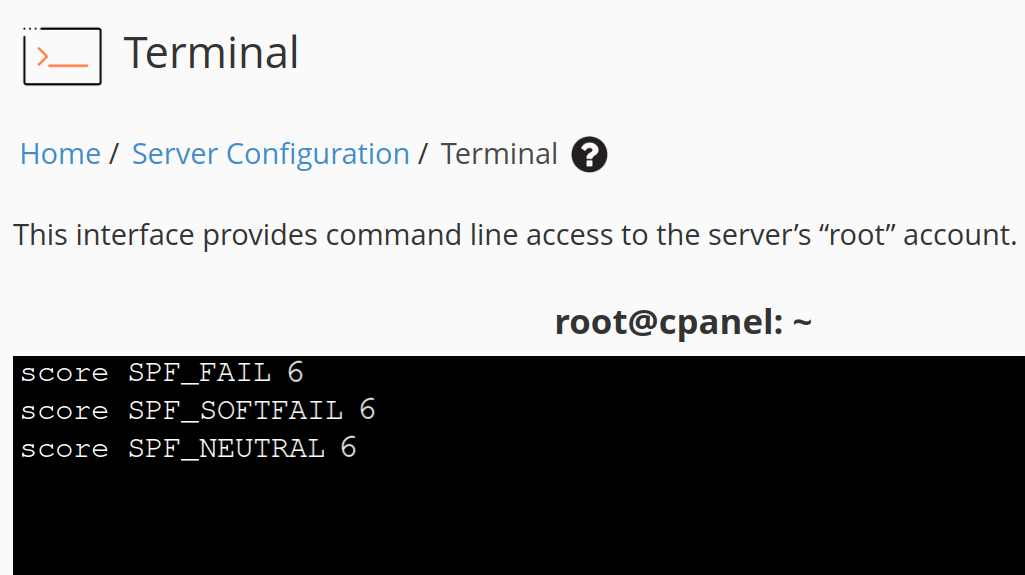
Once complete, save your edits and restart the SpamAssassin service for these updates to take effect by running the following script.
/usr/local/cpanel/scripts/restartsrv_spamd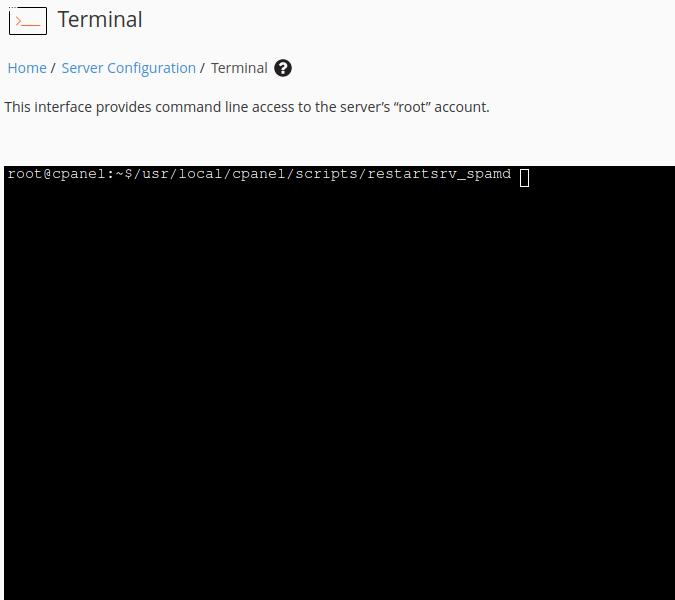
At this point, this SPF Verification Email Security Policy has been implemented on your cPanel server at the global level.
Overwrite SPF Verification Rule Scores at User-Level (cPanel User)
As a cPanel User without WHM Administrator privileges, you can implement this SPF Verification Email Security Policy at the user-level for all email domains under your account. This can be achieved by overwriting the SPF Verification Rule Scores through the Calculated Spam Score Settings.
Simply add new scores for the SPF_FAIL, SPF_SOFTFAIL, and SPF_NEUTRAL Verification Rules with a high score like 6 which exceeds the default and recommended spam threshold score by one to ensure all incoming emails that fail SPF verification are flagged as spam.
After saving the updates, no further action is necessary as these updates take effect immediately. At this point, this SPF Verification Email Security Policy has been implemented on your cPanel server at the user level.
MagicSpam – More Layers of Protection against Spoofed Emails
Despite the built-in protection offered by cPanel, it only takes half the picture into consideration when it comes to addressing the threat of spoofed emails. SPF Verification does not take the From Header into account which has been established as being more dangerous compared to the MAIL FROM. If you’re still getting spoofed emails, then look to an email security solution that recognizes the need to take both the MAIL FROM and From Header into account for the best levels of protection.
MagicSpam is a fully-featured email security solution with multiple layers of protection designed to run on cPanel servers — easy to install and even easier to use. Our policy-based protection allows you to block sources known for sending spoofed emails right at the Simple Mail Transfer Protocol (SMTP) layer which saves on resources. In addition, our PRO version comes with an additional layer of protection with custom content filtering rules which take both the MAIL FROM and From Header into account in order to filter the remainder of spoofed emails that make it through. All of which is supported by an expert team of threat researchers who release daily email security updates.
Conclusion
Spoofed Emails continue to pose an increasingly dangerous threat to businesses. Threat actors are keen to benefit off your misfortune as it is lucrative for them. Without a comprehensive protection strategy against spoofed emails, your business is left vulnerable and at risk. This highlights the important need for businesses to review their security policies and ask themselves the question: How protected is my business against spoofed emails and more generally, email threats.






