Reporting Spam Email to MagicSpam Support: What really happens?

Spam is not only unwelcome and unwanted, it’s a primary platform for phishing and delivering malicious materials. As our teams work hard to combat the ever-evolving threat landscape, new threats can emerge that we haven’t encountered before. Of course, with worldwide distribution, spammers may target specific countries, languages, industries – even individuals like you! When you report spam email to MagicSpam support, you’re helping us in this fight by contributing examples.
“With your examples, we can mitigate threats before others see them.”
With modern-day AI now used to create email content and lures, compromised legitimate email accounts being preempted, and gratuitous amounts of spam leaking from “Too Big to Block” operators, we can only improve filtering and invent new mitigation techniques with actual examples. We welcome and appreciate your support as part of the solution.
One caveat: we need to know that you’re already using our existing default settings. This is why we do not accept samples from, say, your Gmail or Outlook accounts. Only submit emails that get through to your MagicSpam protected server. Use our recommended settings, and only report threats that MagicSpam has not yet identified.
How to report spam to MagicSpam support

If you’re the one in charge of your server and you see ‘uncaught’ spam, we encourage you to report these unwanted emails to our support teams. From there, they are forwarded directly to our in-house spam auditors. As with all support requests, please include your MagicSpam License Key.
When reporting a spam email, the most important thing is to send us the raw file “as an attachment.” Certain email clients, like Outlook, may modify the raw message, stripping away valuable information we need to assess threats and methods used. To do anything about your spam email, our spam auditing and support teams must see the message exactly as it was delivered to your mailbox. As such, we would advise you to use your Webmail (or an email client that will not modify the message).
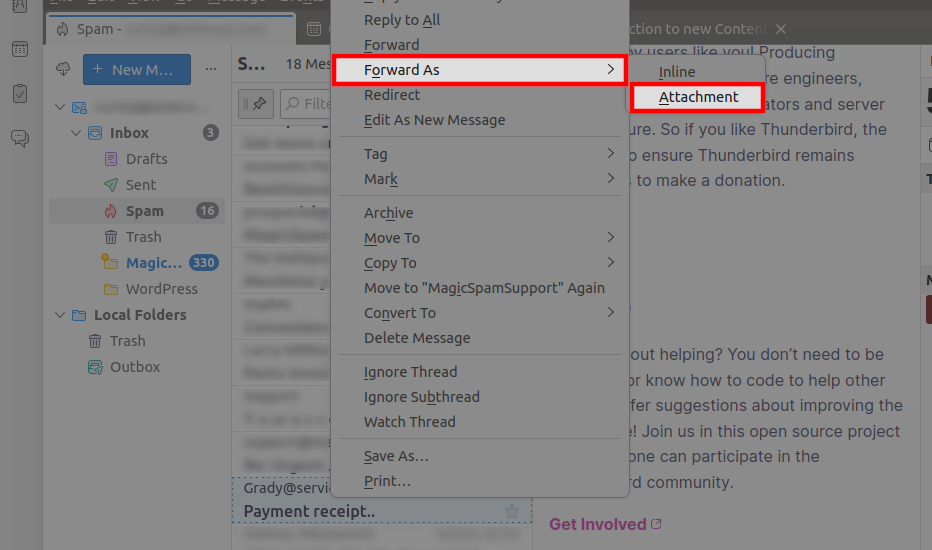
The second most important thing is to check two headers in the raw source. To do this, open up additional options on that email and click View Source in your email client to look for the following:
X-MagicSpam-TUUID: 24244285-e41a-4a82-be6a-fec6607bbbccX-Spam-Status: YesIf you do not see one of these headers, then MagicSpam did not process the email. Every message gets a unique identifier.
You didn’t turn Spam Protection off did you? Globally, Domain Level, or User Level?
If you see that “X-Spam-Status: Yes” header, it has already been marked as spam and should’ve been in your spam folder. If it didn’t appear there, that’s a configuration problem and you’ll need to contact support.
Don’t forget to look at the MagicSpam logs to confirm if MagicSpam saw the message as Ham, Spam, or Quarantine. If it was marked “Ham” and you think it should’ve been marked “Spam,” we’ll want to take a look.
What actually happens when you report uncaught spam to MagicSpam support?
What people define as “spam,” or Unsolicited Bulk Email (UBE), can differ from person to person. As the old adage goes, “one man’s trash is another’s man’s treasure.” Or, in this case, “one man’s spam is another man’s reading material.”
When you report uncaught spam, we take every single case seriously. Spam comes in many forms, from annoying email marketing and soliciting to serious cyberthreats. Our team’s approach varies in accordance based on danger to the public.
Step 1 – Threat Triage
The first thing we do after receiving your reported spam is we triage it. Our teams are constantly addressing new and emerging threats, and we take your reports seriously. Simultaneously, we cannot risk generating false positives. As such, it can take a bit longer to address spam deemed less dangerous unless the volumes are remarkably high. They will address the most dangerous spam first.
Step 2 – IP Reputation Review
Next, we perform an IP reputation review. When you present us with uncaught spam, the information we glean helps us map IP reputation across the internet. Additionally, we share verified information with our IP reputation partners. By doing this, we help both our own customers and email operators worldwide. However, we must make sure we aren’t catching “Too Big to Block” operators like Microsoft and Google. Even with a gratuitous amount of unwanted spam and phishing attempts from Outlook or Gmail, you wouldn’t want to block all email from them, right? Even for a short time.
Step 3 – Platform Analysis
The third step in our process involves an in-depth scan of the spammer’s platform. Before we can dissect the message itself, we must analyze the type of platform that released the spam.
Every legitimate operator knows, if you operate an email server long enough, you’ll eventually have some spam leakage. However, some platforms are designed specifically for spamming. By checking the email headers, we can often identify the tool being used. This is why it’s so important you send your uncaught spam to us as a raw attachment.
Step 4 – Content Examination and Analysis
After our teams finish analyzing the platform, they process the message and analyze its content. They find the spammers’ identities, tools, and methods, and determine how our filters and techniques will stop similar messages now and in the future. This is especially important with content arriving from “Too Big to Block” operators like AWS, Microsoft, and Google.
While spammers can constantly mobilize new templates and content, our threat team can manually (or by way of advanced algorithm implementation) flag the content as suspicious. The spam is often in the form of an attachment, a malicious link, or obfuscated. That said, these techniques can be filtered.
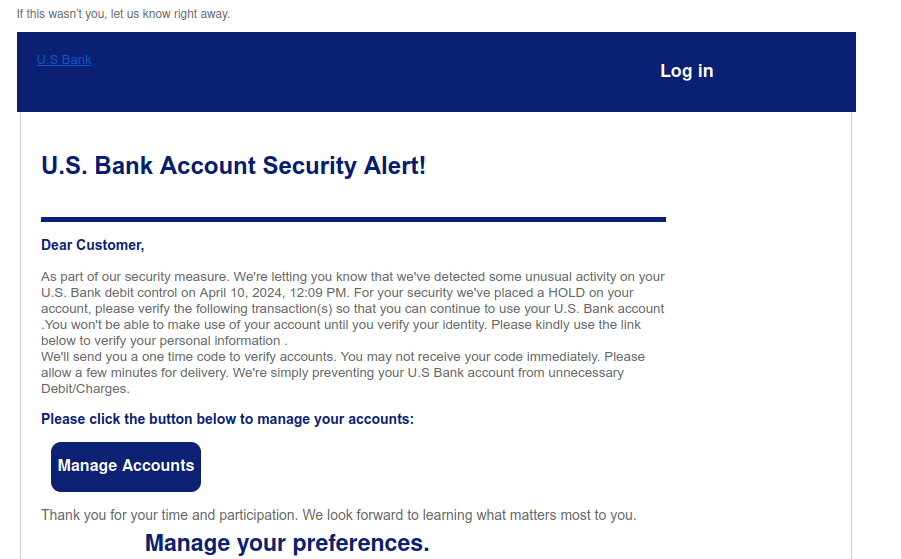

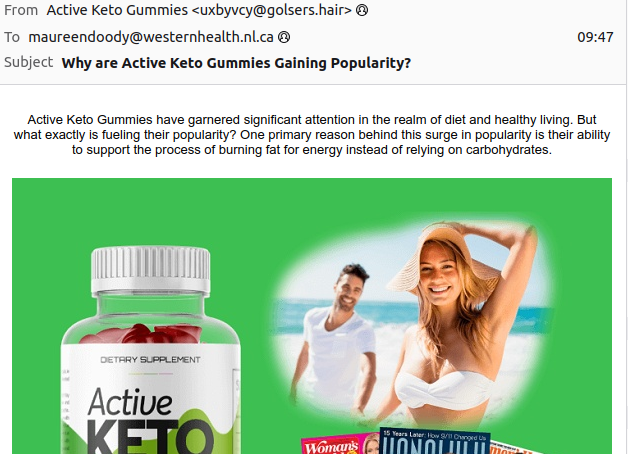
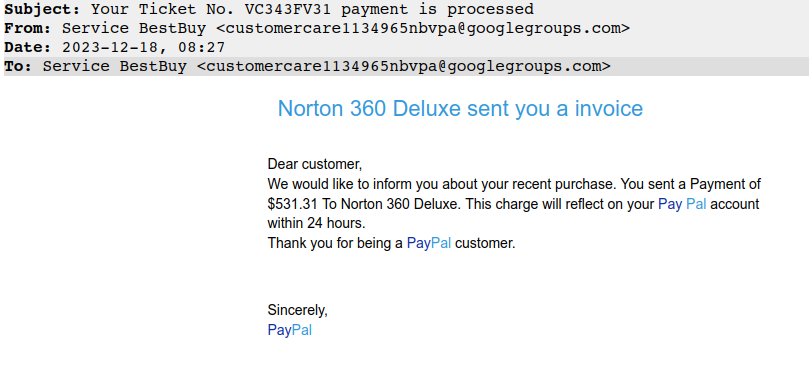
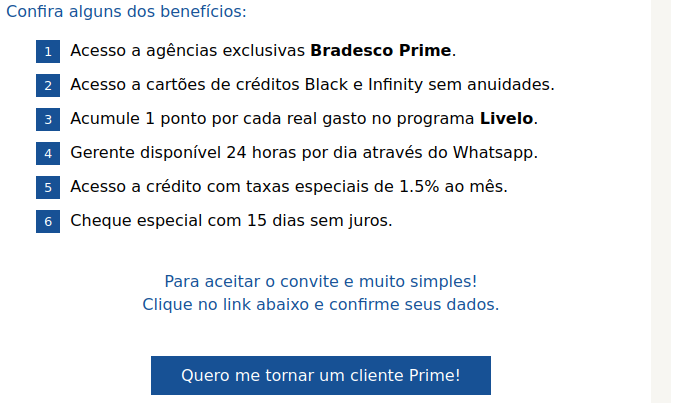
Step 5 – Advanced Filtration Updates
After processing the message, our teams immediately create new, updated filters for previously unseen spam and techniques. This way they can immediately monitor the activity and see if it is prevalent enough for automation. Automation is integral because we don’t want our threat experts putting out new rules for every variant of the content. Instead, we want our automated systems to recognize them in real-time.
Other ways to fight spam in your inbox
Our recommended policies exist to keep you safe. If you’re considering turning off a policy due to a false positive, please check with the support team. It usually isn’t the policy at fault, even though it may seem that way. It could just be an email client/server configuration error.
Any policy that can catch legitimate email is typically set to Flag as Spam. You can typically find those legitimate emails in customers’ spam folders. Remember, when the sending server or company fails to follow industry best practices for sending email, this can happen. That’s what ‘whitelisting’ is for.

If using our custom filters for Apache SpamAssassin, make sure your installation uses the recommended plugins. Also, make sure to set the default score for inbound SpamAssassin filtering to 5.0, and outbound to 8.0.
Other things you can do include disabling “Bayesian;” by default, this reduces the score on all email. You should also avoid sending multiple copies of the same email in the same report.
Final thoughts
Our dedicated teams take spam reports very seriously. They’re comprised of in-house engineers that care about you and your business’s well-being.
We never share any personal or private information included in the email examples you send over. Even so, ensure your policies allow for sharing data with third parties, at least for use in threat protection.
